Secure MCUs and Smart Design Harden Embedded Systems Against Cyber-Hacks
投稿人:电子产品
2012-09-19
Until recently, the term “hacking” usually brought to mind profit-minded criminals and politically motivated groups that seize control of consumer PCs or invade the large centralized computer systems at the heart of both commercial and government organizations. While both these activities remain a real threat, the MCUs that now control everything from point-of-sale terminals to smart utility meters are now popular targets of opportunity for these merchants of mayhem. As a result, embedded systems designers are now caught up in a high-stakes game where keeping hackers at bay has become a basic requirement for virtually any standalone or networked embedded system.
Securing an embedded system requires a multilayered approach that involves everything from the system’s packaging to its software, but the key ingredient is an MCU that can tie it all together. In this multi-part series, we’ll explore some of the ways hackers exploit embedded systems’ vulnerabilities and the features included in security-conscious MCUs that can be used to defeat them.
Tools of the trade
The tools used to build a multilayered defense fall into several categories, many of which can be combined to address a particular threat.
Privacy/Encryption: Encryption techniques such as AES, (3)DES, ARCFOUR, and KeeLoq generate encrypted stream that (theoretically) cannot be read unless the recipient has the corresponding decryption key. While traditionally used to protect data traveling over communication networks, encrypted storage is now also used within embedded systems to prevent exposing the system’s program or data to increasingly sophisticated probing techniques.
Key management: Hack-resistant embedded systems need secure methods of generating, storing, and exchanging encryption keys to keep them from being intercepted (or guessed) by the attacker. Authentication: Digital signatures and authentication algorithms like CBC-MAC and HMAC are used to ensure the device on the other end is the one your device intended to talk to and in this way thwart “spoofing” and “man-in-the-middle” attacks.
Integrity: Hash algorithms such as MD5, SHA-1, SHA-2, and other error detection techniques are used to guarantee data has not been altered or substituted.
Countermeasures to direct assaults: Depending on the application, a system may have several layers of mechanical and electrical barriers to prevent a hacker from gaining physical access to the MCU or its signals. Countermeasures that detect opening of a product’s case, sudden changes in temperature or supply voltage, or other so-called fault-injection techniques usually trigger a mechanism to quickly erase any sensitive data in the MCU’s memory or registers and permanently disable the compromised system.
Secure Code: For similar reasons, embedded systems that may be exposed to direct assaults now employ encrypted memory, physical isolation, and integrity verification techniques to ensure the MCU boots and loads from the intended memory location and executes clean, untampered firmware.
Targets and tactics
For the purposes of this introductory article, we’ll focus on smart utility meters and remote financial transaction terminals. This is because they represent some of the most tempting targets for would-be hackers and because they operate in nonsecure environments and have communication capabilities, both of which provide entry points for hackers. In addition, the techniques used to defend these systems are readily applicable to most other embedded applications.
Since both meters and transaction terminals spend their lives in unsecured environments, physical intrusion is a primary threat vector. Gaining physical access to the circuit board containing the MCU allows an intruder to monitor traffic between the processor and external memory and other I/O or even probe the contents of the processor’s on-chip memories. Direct access also makes it easier to use so-called fault injection techniques such as altering the system clock speed or supply voltage to throw the system into an error state that reveals information about its operation or makes it easier to force the MCU to boot from a block of unauthorized code.
Until recently, physical intervention was usually required to either insert malicious code, insert a device to intercept data, or otherwise probe the reader’s innards. Now however, many new tactics are appearing, often developed by the intelligence community, which enable remote probing of the reader by correlating small variations in the system’s supply voltage or patterns in the EMI it produces with patterns in the bit stream of its encrypted communications. Some of these tactics will be covered in more detail in subsequent articles.
Secure solutions
If you have any question about why network-enabled embedded systems – found in entry points to financial systems such as credit card readers, point-of-sale terminals, and ATMs – are such popular targets for hackers, remember the words of Willie Sutton, a legendary bank robber in the 1920s. When asked why he chose to rob banks for a living, Sutton allegedly replied, “because that’s where the money is.”
While the motivations of cyber-criminals and aspiring terrorists might be slightly different, Mr. Sutton’s observation explains their common interest in exploiting the vulnerabilities of these devices. In most cases, the prize is cardholder information, especially account numbers and PINs which can be quickly monetized using various types of fraudulent transactions. Similar techniques can be used to capture data from smart cards, pay TV SIMs, ePassports, etc., but any of these card systems which employ RF-based, contact-less readers are vulnerable to many other indirect attack vectors.
One of a designer’s primary objectives for payment terminals is to protect the encryption keys that would allow a hacker to extract the identity and payment data contained in the magnetic strip or smart chip on a user’s card. Many leading MCU vendors offer embedded memory controllers with anti-tamper and secure memory security features that make them suitable for payment terminals. Texas Instruments offers several solutions for secure transaction terminals including the Sitera AM3715/3703 series. These ARM Cortex A8-based MCUs are equipped with the graphics and media processing, communication, and security features needed for service in handheld equipment such as POS terminals and medical equipment applications. Among the more notable security features is the M-Shield block that enables a secure application to run in a tamper-resistant environment. TI’s M-Shield mobile security technology includes hardware accelerators that perform authentication and content decryption/integrity checking plus secure state machine (SSM) that applies and guarantees the system’s security policy rules while entering, executing, and exiting from the secure environment.
Atmel’s AT91S051 secure, flash-based microcontrollers also are designed for secure transaction applications. They integrate multiple security mechanisms to guard against hacking and advanced cryptographic algorithms to guarantee financial assets and transactions, preserve intellectual property and individual privacy in applications. Both processors are based on the 32-bit ARM9 processor core found in Atmel’s popular SAM9N and SAM9XE general-purpose MCUs. They share the advanced encryption and security features of Atmel’s AT91SAM9G non-flash ARM9 MCUs plus extensive anti-cloning features to prevent both IP theft and misuse/hijacking of products to gain access to personal info or monetary transactions. The AT91 family’s physical anti-tamper measures include the ability to automatically trigger erasure of its secure memory if a case breach is detected. Its secure BGA package has insulation on all sides to resist electronic probing and an active anti-tamper grid built into the metallization layer which, if tripped, will zero-out the secure memory. The grid remains powered when the device is off.
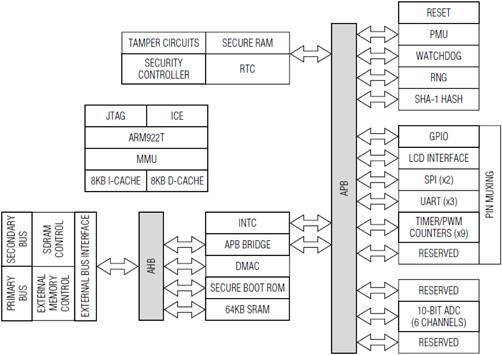
Maxim, for its part, offers an MAXQ series low-power device that combines high-performance, single-cycle processing, sophisticated tamper-detection technology, and cryptographic hardware (Figure 1). Based on the MAXQ30 RISC core, the MCUs are targeted at electronic commerce, banking, and data security systems that require the highest levels of secure access control, secure data storage, digital signature, or certificate authentication. A secure memory protection unit protects critical internal and external memory against tampering with triple-DES (3DES) encryption and an active anti-tamper mechanism.
Smart utility meters represent another top-tier target for less-than-scrupulous entrepreneurs, especially in the emerging economies of Africa, Asia, and Latin America, which have long traditions of energy theft. Besides altering the meter’s readings to lower a customer’s utility bills, creative criminal types of any nationality could use their access to a smart meter to monitor and transmit sensitive information about our consumption that could help them easily determine the best hours to rob a home or business.
Smart meters also raise national security concerns as the electronic warfare activities of both nation-states and extremist groups devote increasing amounts of time and energy on attacking the embedded systems that lie within the utility grids, communication networks, industrial control systems, and other critical parts of modern life we have become increasingly dependent on. Some examples of the mayhem that could be unleashed by hacking smart meters include:
- Commandeering armies of “zombie meters” to transmit misleading information on consumption that could lead utilities to make disastrous decisions about managing their generating capacity and distribution networks. Under-reporting demand by even a few percent could lead to brownouts, blackouts, or worse.
- Using the remote disconnect capabilities available in many modern meters to black out targeted facilities or produce crippling load swings that could bring a power grid to its knees.
- Neither of these scenarios requires access to other smart grid network elements, such as substation switch controls or remotely operated peaking facilities, which could cause even more significant damage.
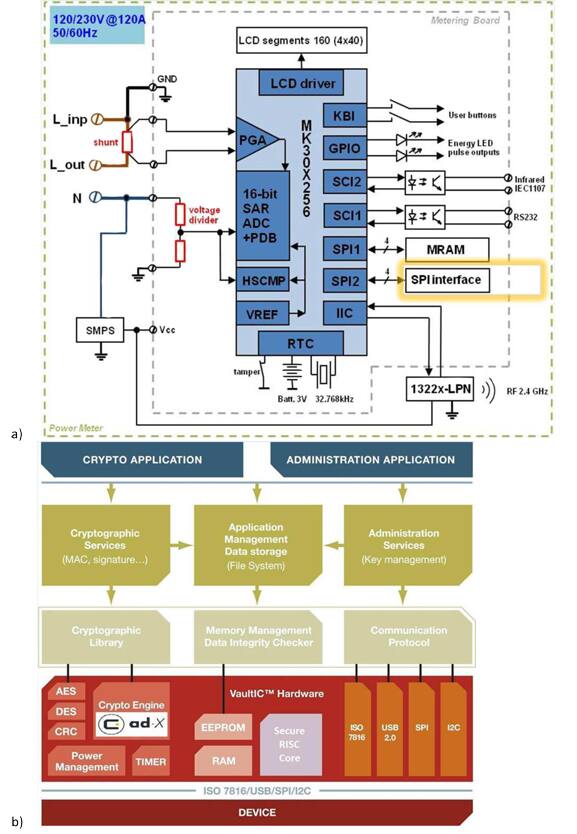
At Design West 2012, Freescale also announced the VF6xx and VF7xx Vybrid families of dual-core processors which contain many features essential to secure meter, energy gateway, and financial transaction terminal designs. Both Vybrid series will contain a Cortex A5 processor to run HMI functions and a Cortex M4 core for application and control functions, plus a collection of hardware cores for connectivity, analog/digital control I/O, and display control. Its on-chip security features include Freescale’s TrustZone architecture for secure transactions and DRM. The Vybrid MCUs will also feature independent secure boot hardware logic for each core which requires a handshake with a key retrieved from the processors’ secure NVRAM before it allows the core to execute any code. This prevents spoofing of software through key authentication or software re-imaging (roll-back attack).
Texas Instruments has been very active in the smart meter/smart energy market for a long time and is developing an extensive line of high-security products for these applications. TI’s LM3S9 and LM3S8 series of ARM-powered Stellaris MCUs have also been equipped with hardware authentication, IP protection, and secure communications capabilities needed in secure smart meter and Energy Gateway applications. Most models also include a memory protection unit (MPU) for secure storage of IP and keys and protection of memory content from inadvertent (or malicious) CPU execution or write functions.
Summary
This article has aimed at familiarizing you with some of the basic issues involved with securing embedded designs and MCUs that will help to protect them. A future installment will cover software and OS issues concerned with protecting against cyber-jacking and data interception. Another upcoming article will provide detailed looks at some of the more advanced threats that are beginning to appear — and the tools that can be used to defeat them.
References:
- “Pacemakers and Implantable Cardiac Defibrillators: Software Radio Attacks and Zero-Power Defenses”
- Maxim Application Note 4809: Designing Next-Generation Payment Terminals That Meet PCI PTS 3.x Requirements
免责声明:各个作者和/或论坛参与者在本网站发表的观点、看法和意见不代表 DigiKey 的观点、看法和意见,也不代表 DigiKey 官方政策。






 中国
中国