Security is the Key to Success for MCU-based IoT Applications
投稿人:电子产品
2015-04-29
As the Internet of Things (IoT) expands, there is growing concern over how to safeguard the massive amount of data transmitted and stored by IoT devices. MCUs that support standard encryption, decryption, and authentication algorithms can help mitigate concerns about data security. It is also increasingly important to protect IoT devices from tampering that can reveal important security information, such as security keys, to defeat security measures. MCUs that support code protection, tamper detection, and other advanced security capabilities can defend devices from these types of invasive attacks.
This article will quickly review the key security capabilities of MCUs you should look for in IoT-oriented designs. Once you understand some of the common capabilities you can better look for the implementation that will offer the best fit for your next design. Some example security-oriented devices will be described to better illustrate the use of key security features in IoT applications.
IoT security basics
Health and fitness is one of the fastest growing set of applications for wearable IoT devices. You can easily measure your heart rate during a workout, save profile data to better plan your exercise regime, and even look for early warning signs of sickness or stress. Management of diabetes can be more easily managed with convenient, wearable IoT devices and soon many blood-related measurements will be possible via non-intrusive means using advanced sensing applications. The availability of all this personal related health data is a boon for staying healthy, but managing access to the data will be critical for personal privacy. You may not want everyone to have access to data that could be used as a real-time lie detector, as just one simple example.
So, if you want to protect IoT data, whether it is for personal health data privacy, financial information, or even just your location during the day, the devices you use will need to implement some security measures. Luckily there are several standard security algorithms and protocols that can be used to effectively protect data during transmission and while stored on an IoT device. Specialized peripherals are available to help implement some of the most useful security functions. Some newer MCUs are even including implementations of these common functions on-chip. The most common security functions are related to encrypting message data, so someone “listening in” to a data transmission cannot understand the message, decrypting message data using a secret key that only the intended recipient knows, and authenticating message data to prove that it has not been tampered with by someone impersonating an authorized sender. These standard cryptographic functions form the basis of virtually all successful security techniques.
Standard cryptographic functions
Some standard cryptographic algorithms are used to encrypt large messages. These “bulk ciphers” use industry standards that have been tested for many years and have been proven to be very, very difficult to break. Standard bulk ciphers you should look for to support IoT security include DES and TDES, (two of the oldest ciphers still in use) and AES-128/-192/-256 (a more robust modern cipher). Authentication-related security algorithms use a CRC-like approach to process and attach a message “summary” that can be included in the message that protects it from modification (any change to the message will “invalidate” the summary alerting the receiver that the message has been tampered with). Standard authentication algorithms include SHA-1/-256, MD-5, AES-GCM, and HMAC.
Modern MCUs have begun to include hardware accelerators, typically in the form of specialized peripherals, to simplify and speed the processing of sensitive data either for storage or transmission. For example, the Microchip PIC32MZ embedded connectivity family (including the PIC32MZ1024ECH100-I/PT) has a hardware Crypto Engine that accelerates common cryptographic functions. A block diagram of the Crypto Engine is shown in Figure 1. Dedicated cryptographic processors for AES, TDES, SHA, and MD5, seen on the right side of the block diagram, are managed by the Crypto finite-state machine (FSM) using local data and read-and-write packet storage. A DMA controller and dual FIFO memories provide additional local storage to make it easy to process data independently for the CPU. This improves overall system performance and frees the CPU to manage higher-level functions.

Figure 1: Standard Cryptographic Functions on Microchip PIC32MZ MCU. (Courtesy of Microchip)
The performance of the various cryptographic engines is shown on the right side of Figure 1 and can be used to match the bandwidth requirements for a specific IoT- oriented application. Notice that the Microchip PIC32MZ achieves over 700 Mbps for even the most complex algorithms making it a good fit for devices that need to send large data sets in real-time or devices that store data and then need to offload the data quickly, when within range of an aggregation or storage device—both common approaches for IoT high-end wearables and intelligent-data-aggregation hubs.
Security peripherals
In some IoT applications it may be more efficient to use a peripheral device to manage cryptographic functions and store security keys. This is particularly useful if the best MCU for the application does not have any built-in cryptographic functions. Authentication-oriented peripherals can also be used on wearable IoT devices that require consumable sensors, such as sensor strips or pads. The low-cost peripheral can be embedded in the consumable and will guarantee the consumable is from a reliable source, works with the measurement device and/or has not been used more than allowed (consumption tracking).
The Atmel ATSHA204A-SSHDA-B, for example, provides secure authentication and validation for both host and client operations. It implements the SHA-256 hash algorithm for message authentication code (MAC) and hash-based message authentication code (HMAC) standards. A guaranteed unique 72-bit serial number helps track units while a 4.5Kb EEPROM can be used to store security keys and data. Multiple IO options allow the device to interface to an MCU using a UART-compatible single-wire interface or a 1 MHz I2C-compatible interface. In the single-wire mode, the device can be powered via the data signal to simplify its use in low-cost consumables.
In order to evaluate, test and develop IoT-related applications Atmel provides a complete development environment. As illustrated in Figure 2, an ATSHA204 or ATAES132 card with sockets for the peripheral devices attaches to a standard MCU evaluation board to create an efficient development environment.
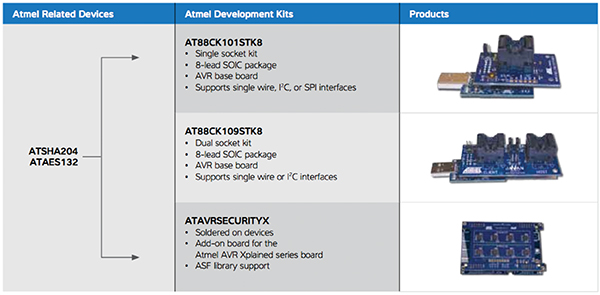
Figure 2: Development Platforms for Atmel ATSHA204 CryptoAuthentication Devices. (Courtesy of Atmel)
Peripheral devices, like the ATSHA204A can be used for several IoT-related applications including:
- Anti-counterfeiting to validate that a removable, replaceable, or consumable client is authentic
- Protecting firmware or media by storing validation code used at boot time to prevent unauthorized modifications or to decrypt downloaded media files
- Exchanging session keys for use by a companion MCU’s hardware crypto engines to manage confidential communications channels
- Storing small amounts of data securely on-chip for configuration, calibration, and consumption of data
- Checking and validating user passwords and setting up secure exchanges with other connected subsystems
Secure MCU using FRAM memory
Some MCUs are even using advanced-memory technology to create an even more secure storage method for secure data. Texas Instruments MSP430FR5969 devices use FRAM to store code and data on-chip. This ferromagnetic memory technology offers much faster read-and-write access to non-volatile memory than traditional flash technologies. Because all operation data can be stored in non-volatile FRAM without performance penalties, sensitive data that needs to be saved between power cycles can be more easily and securely managed. In fact, advanced memory protection functions are available that eliminate the possibility of external memory access to specified memory segments. Only authorized programs can access these memory segments, protecting sensitive data from external hacking and tampering.
The MSP430FR5969 MCUs also provide an AES acceleration engine that can further speed processing of secure data. The AES accelerator block, shown in the blow-up of the MCU block diagram in Figure 3 below, processes encryption functions from between 168 cycles to 234 cycles depending on the “flavor” of AES being processed. The inclusion of local AES state memory and key memory, within the accelerator and the use of DMA for common cipher-mode operations reduces the need for CPU intervention to dramatically improve system efficiency.

Figure 3: AES Crypto Function Support in TI MSP430FR5969 MCU. (Courtesy of TI)
DMA operations are intelligent enough to implement the chaining needed to move a complete message through the AES engine without any CPU intervention. Multiple DMA channels can be allocated and block-cipher operations (of which many are needed to process a complete message) can be automatically triggered when each sub-block has been processed and the next sub-block of data is available. Only after the entire message has been processed does the CPU need to be notified. This makes it easy to separate cryptographic functions from regular functions and helps insure that there are no opportunities to “leak” cryptographic information that could help a potential hacker.
Trust architecture and tamper protection
IoT wearable devices are likely to be targets for hardware tampering since it is easy to gain access to one. Unlike traditional networked equipment, like servers and switches, which can be protected from hardware-based attacks by limiting access to authorized personnel, it will be easy to buy IoT devices and tamper with them using sophisticated equipment, if the payoff is big enough. Luckily MCU manufacturers have started adding specific hardware features to help detect and report tamper events that could indicate a hacker is trying to probe your MCU in an unauthorized manner.
The Freescale Kinetis family of MCUs (e.g., the MK21DX128) has a dedicated Tamper Detect module, shown in the lower left corner in Figure 4 that provides secure key storage with internal and external tamper and physical attack detection. The tamper-detect module includes several key tamper-detection features including:
- 32-bytes of secure storage that reset when a tamper event is detected
- Tamper time register that records the time of a detected tamper event
- Two active tamper shift registers that can be used to detect hardware tamper events
- Up to 10 internal tamper sources including time-counter overflow; voltage, temperature, and clock out-of-range; and flash-security disable and test-mode entry
- Up to 8 external tamper pins capable of generating interrupts on a tamper event
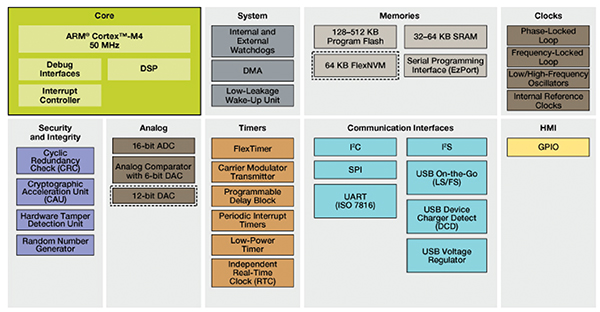
Figure 4: Freescale Kinetis MK21DX128 MCU Block Diagram. (Courtesy of Freescale)
Protecting your MCU-based design from tampering is an important feature that protects your customer’s data from being stolen. Tamper detection can also be used to make sure that the code for your design, stored in the host MCU, is not reverse-engineered and stolen as well. After putting in years of development effort you want to make it as difficult as possible for an adversary to copy your code to leverage your work without paying the cost. Tamper protection can keep your IoT device from being copied or cloned, and then put on the market by a competitor. Protecting your customer’s data as well as your design could both be critical for a successful IoT design.
Conclusion
There are many reasons why it’s important to use MCUs with advanced security features in IoT applications, and implementing both data and design security to secure IoT devices, requires the selection of the right MCU. Only a thorough understanding of the key security features available in a variety of MCUs will allow you to select the right MCU for your application.
For more information about the parts discussed in this article, use the links provided to access product information pages on the DigiKey website.
免责声明:各个作者和/或论坛参与者在本网站发表的观点、看法和意见不代表 DigiKey 的观点、看法和意见,也不代表 DigiKey 官方政策。





