Security in Energy Harvesting Systems
投稿人:DigiKey 欧洲编辑
2015-03-18
Security is becoming a vital element of any roll-out of the Internet of Things, but it adds additional processing cycles and power. This presents a challenge to designers harvesting energy from the environment for their sensor nodes. This article looks at the sources of energy harvesting power, the resulting energy budgets and how this influences the encryption architecture, from encryption at the node to the gateway, and the choice of controller.
The Internet of Things is leading to an explosion of different types of sensors, but this is driving conflicting requirements on system designers. On the one hand, these sensors need to last for years on a battery, or have no battery at all, while on the other hand they have to communicate with the rest of the world, and communicate securely.
This secure communication can be severely challenging for ultra-low-power sensor nodes. Devices that are powered by energy harvested from the environment have very little power left over for wireless communication, let alone the processing of complex encryption algorithms. However, the same factors that are driving the increasing use of such sensor nodes are also driving the need for security. While it may not seem important to secure the connection to a the valve of a radiator or water supply, the information about the use of the heating system can show whether a home is occupied or empty, making it a target for thieves. Even more important is securing remote actuators such as window locks – a vulnerability that allows a hacker to release a window or even a door at will is a major security risk.
Therefore, security is an increasingly important factor in nodes that are powered by energy harvesting, and this changes the way such systems are designed.
A key challenge is that such systems need to use the most secure technologies, which also take the most processing power. No longer is it appropriate for a sensor or actuator node to use lower performance encryption techniques such as WEP or WPA, as these are easily cracked. Now the requirement is for the same 128-bit AES encryption that is found in the rest of the network.
The AES encryption of a single 128-bit block of data using a 128-bit key requires approximately 2109 clock cycles on a generic ARM 32-bit processor, while the decryption of a single block can take 2367 cycles and the key scheduling needs around 670 clock cycles. All of this has to be taken into account in the power budget of the wireless node.
While AES is more computationally intensive than other encryption algorithms such as RC5, there is an advantage that the processing power is catching up with the requirements. More modern 32-bit processors are able to handle the overhead, and there are now controllers with dedicated AES blocks that can handle the core processing in fewer cycles. This makes the implementation of a secure link more viable for systems powered by the environment, but still presents significant challenges.
Using energy sources such as solar cells allows energy to be stored in a lithium ion battery and used with a relatively standard power management system. The eZ430-RF2500-SEH from Texas Instruments is a complete Solar Energy Harvesting development kit to help create a perpetually powered wireless sensor network based on the ultra-low-power MSP430 microcontroller. This includes a high-efficiency solar (2.25 in x 2.25 in) panel optimized for operating indoors under low-intensity florescent lights, which provides enough power to run a wireless sensor application with no additional batteries. Inputs are also available for external energy harvesters such as thermal, piezoelectric, or another solar panel.

Figure 1: Solar power is a key source of energy for nodes on the Internet of Things and the eZ430-RF2500-SEH development kit from Texas Instruments helps designers develop secure systems.
The system also manages and stores additional energy in a pair of thin-film rechargeable EnerChips storage devices that can provide enough power for 400+ transmissions. The EnerChips act as an energy buffer that stores the energy while the application is sleeping and has light available to harvest.
The eZ430-RF2500 is used to run the energy-harvesting application. As a complete USB-based MSP430 wireless development tool it provides all the hardware and software necessary to use the microcontroller and 2.4 GHz wireless transceiver, including the security protocols. It includes a USB debugging interface that allows for real-time, in-system debugging and programming for the MSP430. The integrated temperature and RF signal strength indicators can be used to monitor the environment
For other power sources, the energy can fluctuate much more widely and requires a more sophisticated power management system. The SmartMesh node from Linear Technology can take the output of a thermal Peltier-effect generator (for example on a radiator) to deliver power to the wireless node. Being able to deliver the peak current at the right time is a key requirement for supporting the processing for the encryption on top of the packet handling and RF transmission.
One company that has recognized this challenge in energy-harvesting systems is EnOcean. It has been at the heart of both wired and wireless self-powered sensor nodes using the energy of motion, indoor light and temperature differentials. In addition to its fundamental security measures, EnOcean has developed an expanded security concept that includes two new functions, "Rolling Code" and "Encryption". This offers an additional level of security that is particularly important for sensitive systems such as smart homes or smart metering.

Figure 2: EnOcean's development kit includes secure modules that can be powered from a range of energy sources.
A major application of EnOcean’s batteryless wireless technology is building automation. Products and systems set up on the energy harvesting, maintenance-free technology can be integrated in all common building automation solutions – and are also able to communicate over LON, KNX, BACnet, TCP/IP or Ethernet. Security plays an all-important role in these networks. Wireless systems need to be guarded by suitable measures so that access is only granted to those who are authorized.
The EnOcean modules already have security measures such as checksum to avoid transmission errors, and each module has a unique 32-bit identification number (ID) that cannot be changed or copied, which protects against duplication.
Rolling Code is an additional capability where an EnOcean wireless node counts all incoming and outgoing data packets continuously to ensure the integrity of the telegrams. A 16-bit rolling code (RC) incremented with each telegram is generated as a constantly changing (i.e. rolling) security mechanism. The telegram header, telegram data and current rolling code are used to calculate a 32-bit message authentication code (MAC). The receiver system can then validate the data packet on the basis of the code.
EnOcean has also been looking at how the encryption can be optimized for IoT nodes, given all the challenges. It is using either the ARC4 algorithm (Alleged Ron’s code 4) with a 32-bit key or, for higher security needs, the AES algorithm with a 128-bit key. Device manufacturers can combine the rolling code and encryption mechanisms to suit individual needs and so implement different security levels flexibly according to the demands of the respective solutions.
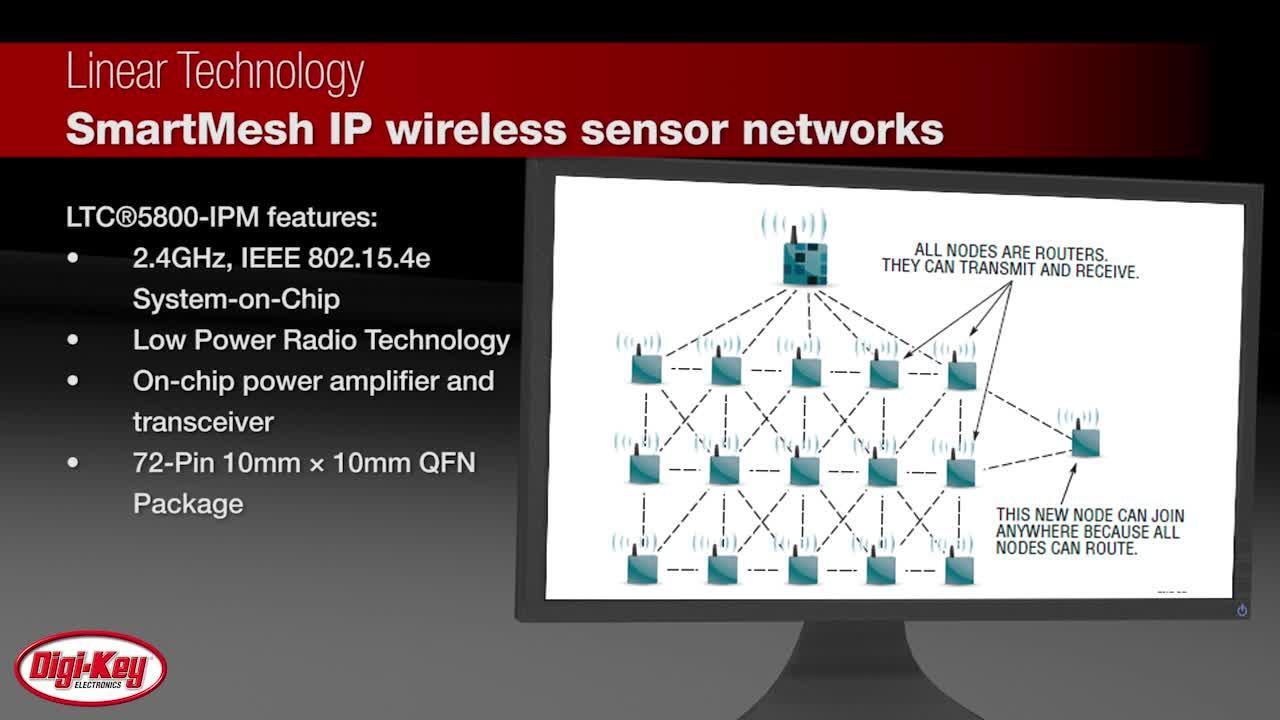
Linear Technology is involved in the wireless node in other ways through its controllers developed by Dust Networks. The SmartMesh network architecture is based on Dust Networks’ Time Synchronized Mesh Protocol (TSMP), a full networking stack that is compatible with the IEEE 2.4 GHz 802.15.4 2006 radio standard. This includes a Time Slotted Channel Hopping (TSCH) media access layer (MAC) that works by dividing time into ‘slots’, and providing a mechanism to map timeslots to channels with a pre-assigned hopping sequence.

Figure 3: The SmartMesh node from Linear Technology is optimized for energy-harvesting applications and includes three levels of security.
This means the nodes know precisely when to talk, listen, or sleep, packet exchanges are synchronized with no collisions on the network, and every packet is scheduled and synchronized for energy efficiency with no extra preamble (on the transmission side) or guard interval time (on the receive side).
This has allowed security to be added at the physical level so that all the traffic is protected by end-to-end encryption, message integrity checking, and device authentication. The SmartMesh network manager also contains applications that enable the secure joining of the network, key establishment, and key exchange. There are three increasingly strong levels of device authentication, 128-bit AES support with multiple keys as well as synchronized key changeovers where the entire network changes over to a new key automatically. This can be customized by the network operator, trading off extra security with additional network traffic and the power budget available.
All of this is integrated into the Eterna system-on-chip devices that power the Dust nodes and have the power management optimized for energy harvesting sources and Direct Sequence Spread Spectrum (DSSS) radios compliant to the IEEE 802.15.4 standard in the 2.4 GHz band.
Conclusion
There is a fine balance between the power requirements and security implementation of nodes in the Internet of Things, especially for systems powered by the energy from the environment. Microcontroller technology has caught up with the needs of the designer allowing the latest AES encryption technology to be practical in energy-harvesting designs, and this is helping to drive the adoption of secure systems.
免责声明:各个作者和/或论坛参与者在本网站发表的观点、看法和意见不代表 DigiKey 的观点、看法和意见,也不代表 DigiKey 官方政策。








 中国
中国